National Counterintelligence and Security Center
NITTF Produced Guides & Templates
This section of the resource library provides guidance developed and produced by the NITTF, including the Any Given Day Video and the 2017 Insider Threat Guide. For additional information please contact This email address is being protected from spambots. You need JavaScript enabled to view it..
NITTF Guides and Multimedia:
| 2017 NITTF Insider Threat Guide | Protect Your Organization Guide |
| 2017 Insider Threat Guide: A Compendium of best practices to accompany the National Insider Threat Minimum Standards Errata |
Protect Your Organization from the Inside Out: Government Best Practices (PDF) |
| Any Given Day Video |
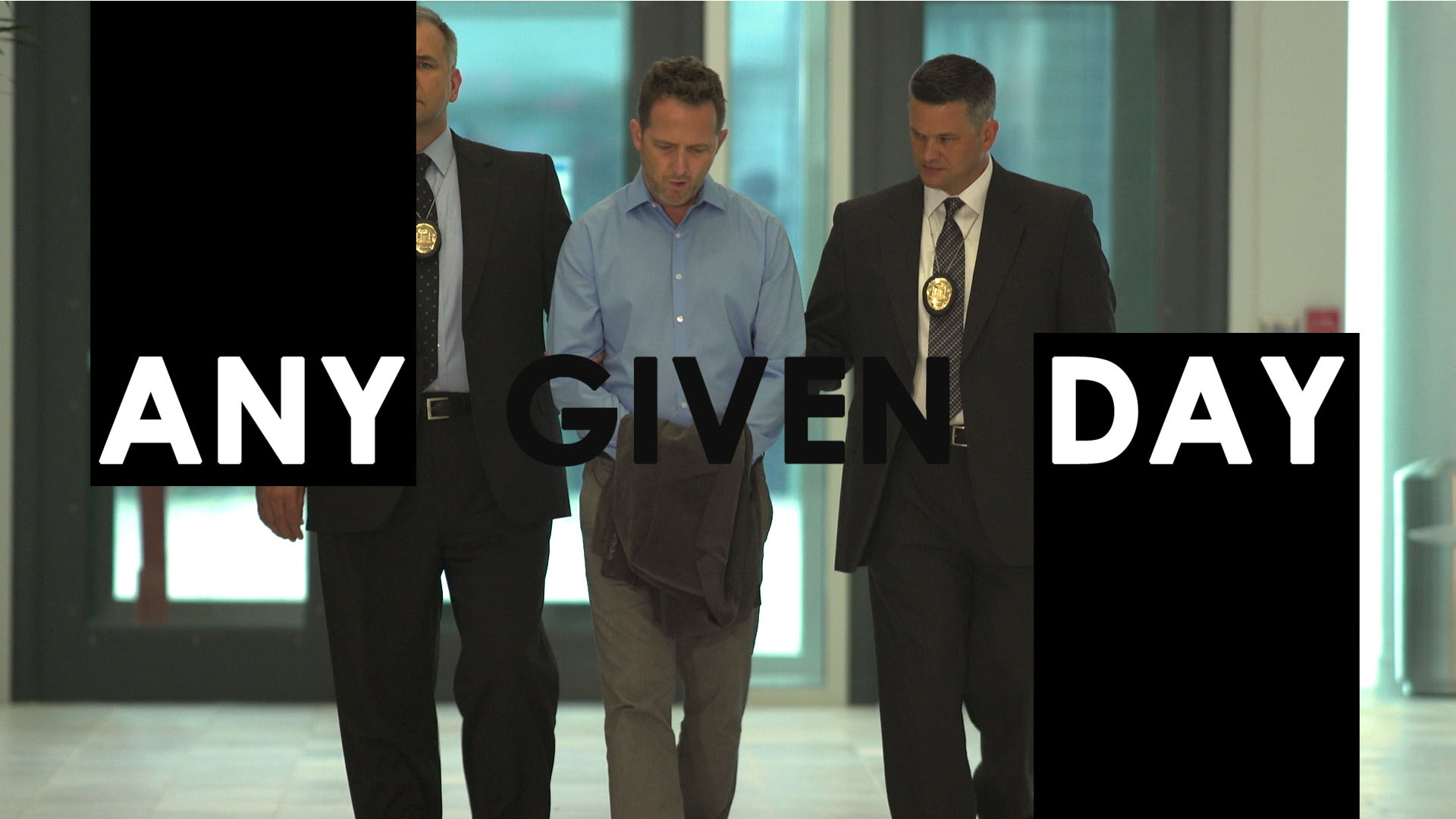 |
| Click the image to view the video |
|
Any Given Day (VIDEO) is an 8-minute video that was produced to enhance insider threat education and awareness. It highlights the balance between collecting information and privacy concerns and presents a side of insider threat programs that is not often considered: protecting national security at the human level. Executive Order 13587 focuses on safeguarding classified networks and classified information, but it's not just about information; it's also about protecting people. NITTF encourages inclusion of this video in your existing training plan for your workforce. |
NITTF Technical Bulletins
NITTF has developed Technical Bulletins that identify key technical issues in developing an Insider Threat program. Please click on the NITTF Technical page to review these bulletins.
Additional NITTF Guides and Templates
- Insider Threat Program Inquiries Handbook*
- Insider Threat Cost Model Template*
- NITTF 2014 Guide to Accompany the National Insider Threat Policy and Minimum Standards*
- (New) A Capabilities-Driven Framework for Threat Mitigation*
* This material is For Official Use Only and has not been approved for public release. Please contact the NITTF if you have an official need for this item.
For Additional guidance on Assessment Information please refer to the NITTF Assessment Page.
NITTF Technical
![]()
The NITTF Technical Team is a vital component of the NITTF through its infusion of specialized expertise into other NITTF teams/work-streams as well as its development of effective and cost-effective technical solutions for the insider threat community. The Technical Team provides tailored assistance to inside threat programs spanning the IC, DoD, and NT-50 Federal Partners focusing on User Activity Monitoring (UAM), insider threat data integration and analysis, automated case management, Enterprise Audit Management (EAM), and other technical capabilities. The Technical Team also brokers classified network provider/subscriber relationships across the USG, maintains awareness of the vendor marketplace to identify tools and best practices, provides input to national-level policy frameworks, and explores solutions for emerging technical trends and vulnerabilities.
The NITTF Technical Team developed technical bulletins to provide the insider threat community additional information on key technological issues departments and agencies face when implementing insider threat programs. Bulletins are arraigned by the date of bulletins with the most recent on top. As new bulletins become available, they will be identified as new and placed on the top of the list. Click on the title to view the technical bulletin. For additional information contact the NITTF Technical Team.
| Title | Date of Bulletin |
|---|---|
| How CNSSD 504 Defines UAM | 5/27/2018 |
Abstract: This Tech Bulletin considers the definition of user activity monitoring (UAM) provided by CNSSD 504, and it notes the technical functionality that a UAM solution must have to meet the Directive’s requirements.
| Title | Date of Bulletin |
|---|---|
| How CNSSD 1015 Defines EAM | 4/27/2018 |
Abstract: This Tech Bulletin considers the definition of enterprise audit management (EAM) provided by CNSSD 1015. According to CNSSD 1015, EAM is the "the identification, collection, correlation, analysis, storage, and reporting of audit information, and monitoring and maintenance of this capability."
| Title | Date of Bulletin |
|---|---|
| Security Information and Event Management for Insider Threat Programs | 3/22/2018 |
Abstract: Security information and event management (SIEM) refers to a cyber tool for the collection and analysis of security events and threat management.
| Title | Date of Bulletin |
|---|---|
| Data Quality for Insider Threat Programs | 1/5/2018 |
Abstract: Executive branch departments and agencies should not overlook the importance of data quality to their insider threat programs. Inaccurate or ‘poor-quality’ data can hinder a program’s ability to identify theta behaviors and conduct an effective inquiry.
......................................................................................................
Provided below are additional technical bulletins that are not available for public release. Please contact NITTF if you have an official need for this item.
| Title | Date of Bulletin |
|---|---|
| Directive on Protecting National Security Systems from Insider Threat (CNSSD 504 w/ Annex C) | 09/15/2016 |
Abstract: This is the latest version of CNSSD 504 which adds Annex C, Privileged User and Privileged Access Controls
| Title | Date of Bulletin |
|---|---|
| Continuous Monitoring and Continuous Evaluation and Their Value for insider Threat Programs | 3/31/2018 |
Abstract: No abstract information available.
| Title | Date of Bulletin |
|---|---|
| Clarification of User Activity Monitoring (UAM) Requirements | 2/25/2018 |
Abstract: No abstract information available.
| Title | Date of Bulletin |
|---|---|
| User (Entity) Behavior Analytics for insider Threat Programs | 2/14/2018 |
Abstract: Executive branch departments and agencies may want to implement a UBA/UEBA tool to enhance their ability to find, track, and mitigate anomalous activity.
| Title | Date of Bulletin |
|---|---|
| The Provider/Subscriber Relationship | 2/10/2018 |
Abstract: No abstract information available.
| Title | Date of Bulletin |
|---|---|
| UAM Solutions for insider Threat Programs | 2/10/2018 |
Abstract: No abstract information available.
| Title | Date of Bulletin |
|---|---|
| Commercial Data Aggregators for Insider Threat Programs | 1/30/2018 |
Abstract: No abstract information available.
| Title | Date of Bulletin |
|---|---|
| Cross Domain Solutions for Insider Threat Programs | 1/14/2018 |
Abstract: Executive branch departments and agencies that operate multiple classified networks may want to employ a Cross Domain Solution (CDS) with their UAM solution(s) to transfer information between two or more differing security domains.
![]() Videos
Videos
Cyber Explore - Fundamentals of Cyber
This learning experience is designed for professionals new to the cyber realm. It introduces users to the computer's component layers and associated functions, virtualization concepts, and security methods.
Cyber Aware – Anatomy of a Hack
This learning experience is designed to increase awareness of the protocols that defend information systems and data. It demonstrates to users where network and system vulnerabilities may be while also helping them to understand common hacking methods.
Cyber Exploits – Understand the Threat
This learning experience is designed to increase understanding of the broader categories of cyber-attacks. It introduces specific terminology and real-world applications so users can recognize the threat when they see it.
Federal Partners Outreach
The following materials are provided to support Federal government department and agencies in countering foreign intelligence threats. All materials may be downloaded. For questions about the materials, please contact the Federal Partner Outreach Team via email This email address is being protected from spambots. You need JavaScript enabled to view it..
Federal Partner Newsletters
- April Newsletter 2019
- July Newsletter 2019
- October Newsletter 2019
- January Newsletter 2020
- September Newsletter 2020
- December Newsletter 2020
- April Newsletter 2021
- May Special Edition Newsletter 2021
- July Newsletter 2021
- October Enterprise Threat Mitigation Newsletter 2021
- January Enterprise Threat Mitigation Newsletter 2022
Resources
This briefing will enable CI and Security officials within USG departments and agencies to brief employees and contractors on foreign intelligence threats, potential vulnerabilities, and the steps that should be taken to safeguard classified and sensitive information. This instructor-led briefing, is designed to allow individual organizations to determine which modules are applicable to their workforce. So, for example, if an organization does not have any employees who travel abroad, that module can be removed from the briefing.
CFIT Workforce Awareness Briefing (108 MB PowerPoint File)
The following materials are provided to support Federal government department and agencies in countering foreign intelligence threats. All materials may be downloaded. For questions about the materials, please contact the Federal Partner Outreach Team via email This email address is being protected from spambots. You need JavaScript enabled to view it..
Resources